As the cyberattack on the Ukraine grid showed the world, electric utilities are the new target for cyber terrorism. A survey conducted by the website Utility Drive reflects the industry’s rapidly growing concern. In 2015 and 2016, utilities ranked threats from physical and cyberattacks as their sixth largest challenge. In 2017, these threats jumped to number one.
As cyberattacks on the grid become more common and more successful, the power industry is actively looking to understand and reduce their vulnerabilities. My research has identified three areas that offer practical risk reduction against this growing threat.
Modernize cyber defenses
The power industry is highly regulated. Among other things, this regulation includes specific requirements for cybersecurity. This is one of the reasons the industry ranks highly in terms of its security processes. The problem is that achieving these clearly laid out security guidelines gives regulators and utility execs a false sense of safety. Cybersecurity is a lot more like a fencing match than building a castle wall – the threats are constantly shifting and there is no single solution that keeps you safe. For example, while utilities lead other industries in many areas of security, they come up short in others. A survey by Cisco shows that utilities trail other industries with only 33% of utility respondents saying they use access control and authorization security measures.
An industry insider shared a story that illustrates a particularly challenging part of securing electric grids. He told me a well-respected utility he worked with had purchased a suite of advanced cyber defense tools. The company had successfully piloted the tools in several plants. The C-level execs signed the contract and told their staff to roll it out to all their plants. The execs checked the box and thought they were done. Unfortunately, it turns out that utilities are very decentralized. The decisions about how and when to implement cyber technology are actually made at each individual plant. He said plants have a lot of competing priorities and often lack sophisticated IT personnel. The cyber defense tool vendor was left with a large contract but no ability to deploy their tools. Most of the plants were dragging their feet. Even after a year, almost no new deployments had followed the pilots. The exec thought they were secure but the utility remained as vulnerable as ever.
GET MONTHLY NEWS & ANALYSIS
Unsubscribe anytime. We will never sell your email or spam you.
Diversify vendors
Corporations love to limit the number of vendors. It simplifies their operations and training.
It maximizes their volume discounts. It makes managing spare parts easier. Utilities are no different. This is why the Ukraine grid operator had the same industrial control computers at each of the 30 substations that got hacked. This is also the reason that most of the US utilities use the same controller, too.
This approach makes sense from an operations and cost savings point of view. The problem is that hackers love this. All they have to do is get their hands on one of these popular controllers. They can take it apart, figure out how it works, and find its vulnerabilities. Once discovered, their hacking tactics will work across the world.
The best defense is to simply use different suppliers and different hardware. This raises the costs and time hackers have to invest to find vulnerabilities. Imagine if those 30 Ukraine substations used 5 different controllers. If hackers had to work five times harder to take out those 30 substations, they might have narrowed the impact of their attack or even decided it was too much trouble to bother.
Embrace local energy
To hackers, giant power plants and huge corporations look like sitting ducks with targets on their back. These monolithic entities are like virtual Walmarts – once you get through the door, you can get pretty much anything you want. The best way to reduce cyberattacks is to shift away from the century-old model of the centralized grid. Fortunately, this is already happening. The industry is rapidly embracing distributed generation, or what we call Local Energy. While DG is being done largely for resiliency, cleaner energy, and cost savings, it also makes the grid more secure.
Let me explain.
Imagine the grid as a wall of balloons.
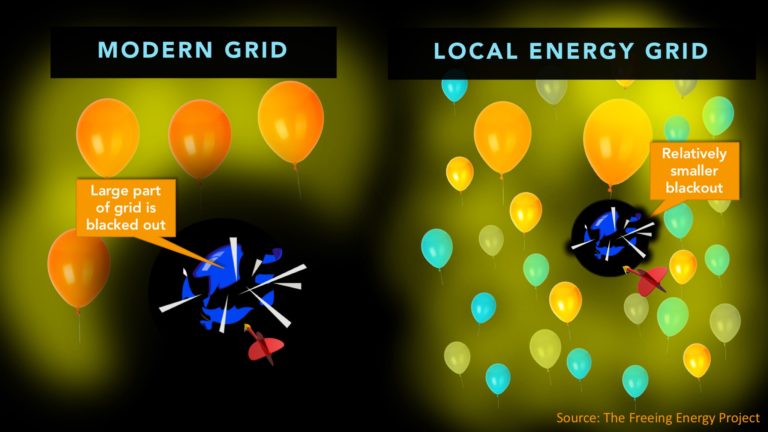
 Today’s grid is like a small number of very large balloons. Each big balloon is like a utility or a large group of substations. Each balloon provides power for the communities around it. Hackers love this.
Today’s grid is like a small number of very large balloons. Each big balloon is like a utility or a large group of substations. Each balloon provides power for the communities around it. Hackers love this.
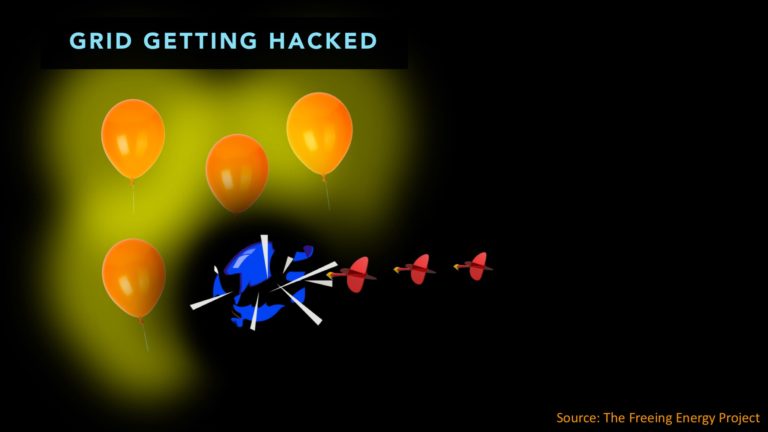 All they have to do it is get past the security defenses of just one “balloon” and they can take out a good portion of the grid. Everything in that area goes dark.
All they have to do it is get past the security defenses of just one “balloon” and they can take out a good portion of the grid. Everything in that area goes dark.
Now imagine a different kind of grid.
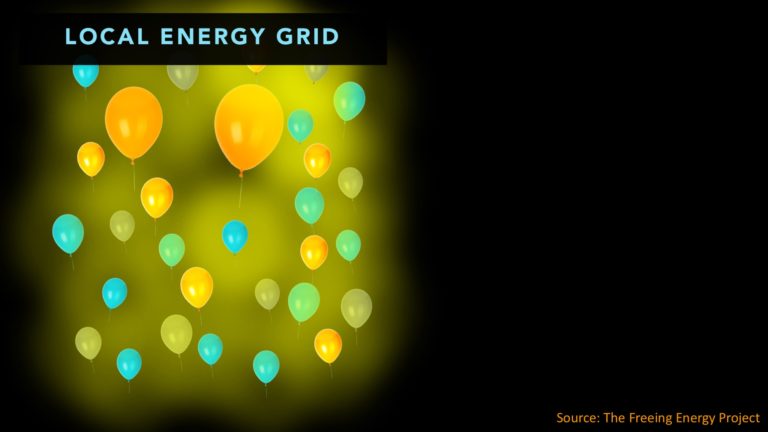 Imagine a local energy grid with many smaller balloons, all interconnected. Together, these small balloons are still serving the same number of customers. These smaller balloons provide a much smaller point of attack.
Imagine a local energy grid with many smaller balloons, all interconnected. Together, these small balloons are still serving the same number of customers. These smaller balloons provide a much smaller point of attack.
Taking out one balloon or even a handful has a proportionately much smaller impact on the overall grid.
The Freeing Energy perspective
The security industry has a saying:
There are two kinds of organizations. Companies that know they’ve been hacked and companies that haven’t yet figured out that they’ve been hacked.
Their point is that everyone has been hacked, even if they don’t know it.
As security breaches flood the news, it’s clear that determined hackers can get inside any computer system they target. The best cyber defense strategy goes beyond just trying to keep hackers out. It’s also necessary to design the system so that, when hackers do get in, they can do the least damage. Interconnected local energy systems make hackers work much harder to take down a good portion of the grid. And, coupled with applying industry best-practices to cyber defense, utilities have a real shot at keeping outages contained and short term.